Openssl Pkcs11 Engine Slot
Posted By admin On 21/03/22Openssl Pkcs11 Engine Slot 8,3/10 9164 votes
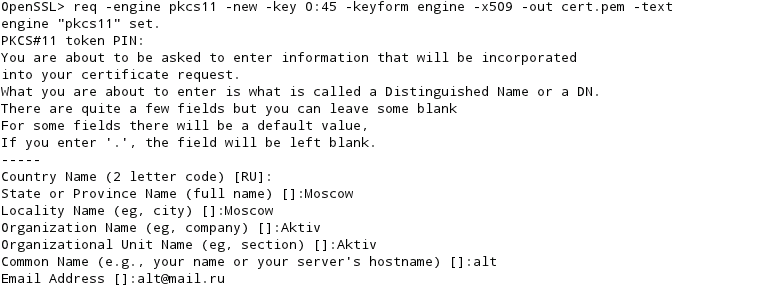


The PKCS#11 Engine. A new PKCS#11 engine has been included with ENGINE name pkcs11. The engine was developed in Sun and is not integrated in the OpenSSL project. The PKCS#11 engine is configured to use the Oracle Solaris Cryptographic Framework. See cryptoadm(1M) for configuration information. Popular CSharp API examples. Pkcs11-id-type label pkcs11-id 'AUTH05B436961C5E5F6D2B' Id: pkcs11-id-type id pkcs11-id '41 54 5f 4b 45 59 45 58 43 48 41 4e 47 45 1b ed 81 a2 96 62 24 c4 a8 0a f1 42 48 10 e6 5d 00' X. # EAP-TLS using private key and certificates via OpenSSL PKCS#11 engine and # openCryptoki (e.
2004-10-21 15:03:30 UTC
Openssl Engine Tutorial
Hello,
First: I am a brand new user of opensc, and English is not my native language .
I have been trying to use etoken PRO with openssl on Linux and Windows.
The Linux implementation using the openssl+engine_opensc.so seems to work for me, knowing that I initialize the token using opensc.
But we are shipping these token to clients that use it in windows. These token have been initialized using Official PKCS11 from Alladin (eTpkcs11.dll), wich does not seems to play well with opensc.
I did try to use the etpkcs11.dll of Alladin with the statically linked version of opensc on windows (win32bin_stat_18_10_2004.zip), but get several errors, both with pkcs11-tool or with engine_pkcs11.dll.
The same eToken seems to work correctly in Firefox after registering eTpkcs11.dll and using a the token initialized with opensc and opensc-pkcs11.dll it work too.
Is this a known problem (I guess yes ;-/) and is someone able to provide a fast solution? (free or not ;-)
C:toolsopensc>pkcs11-tool.exe --module etpkcs11.dll --pin 123456 -O -v
Certificate Object, type = X.509 cert
label: Unlabeled
ID: 39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30
Public Key Object; RSA 1024 bits
label: eTCAPI public key
ID: 39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30
Usage: encrypterror: PKCS11 function C_GetAttributeValue(DECRYPT) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)
Aborting.
C:toolsopensc>openssl
OpenSSL> engine dynamic -pre SO_PATH:engine_pkcs11 -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:etpkcs11.dl
l
(dynamic) Dynamic engine loading support
[Success]: SO_PATH:engine_pkcs11
[Success]: ID:pkcs11
[Success]: LIST_ADD:1
[Success]: LOAD
[Success]: MODULE_PATH:etpkcs11.dll
Loaded: (pkcs11) pkcs11 engine
OpenSSL> engine pkcs11 -pre PIN:123456 -pre VERBOSE
(pkcs11) pkcs11 engine
[Success]: PIN:123456
[Success]: VERBOSE
OpenSSL> req -engine pkcs11 -new -key id_39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30 -k
eyform engine -text -config openssl.cnf
initializing engine
engine 'pkcs11' set.
Found 2 slots
[0] AKS ifdh 0 uninitialized, login (eToken)
[1] AKS ifdh 1 no tok
Found uninitialized token;
PKCS11_get_private_key returned NULL
unable to load Private Key
2676:error:26096080:engine routines:ENGINE_load_private_key:failed loading private key:.cryptoengineeng_pkey.c:117:
error in req
With an other token initialized using opensc, on windows and using the default pkcs11 (engine+dll) everything seems to work:
C:toolsopensc>pkcs11-tool.exe --pin 123456 -O -v
Private Key Object; RSA 1024 bits
label: Private Key
ID: 45
Usage: sign
Certificate Object, type = X.509 cert
label: Certificate
ID: 45
Public Key Object; RSA 1024 bits
label: Certificate
ID: 45
Usage: encrypt, verify
C:toolsopensc>openssl
OpenSSL> engine dynamic -pre SO_PATH:engine_pkcs11 -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:opensc-pkcs11.dll
(dynamic) Dynamic engine loading support
[Success]: SO_PATH:engine_pkcs11
[Success]: ID:pkcs11
[Success]: LIST_ADD:1
[Success]: LOAD
[Success]: MODULE_PATH:opensc-pkcs11.dll
Loaded: (pkcs11) pkcs11 engine
OpenSSL> engine pkcs11 -pre PIN:123456 -pre VERBOSE
(pkcs11) pkcs11 engine
[Success]: PIN:123456
[Success]: VERBOSE
OpenSSL> req -engine pkcs11 -new -key id_45 -keyform engine -text -config openssl.cnf
initializing engine
engine 'pkcs11' set.
Found 8 slots
[0] AKS ifdh 0 login (OpenSC Card (Marc Jadoul (signin)
[1] AKS ifdh 0 (OpenSC Card)
[2] AKS ifdh 0 no pin (OpenSC Card)
[3] AKS ifdh 0 no pin (OpenSC Card)
[4] AKS ifdh 1 no tok
[5] AKS ifdh 1 no tok
[6] AKS ifdh 1 no tok
[7] AKS ifdh 1 no tok
Found slot: AKS ifdh 0
Found token: OpenSC Card (Marc Jadoul (signin
Found 1 certificate:
1 Certificate (/C=BE/L=Bruxelles/O=Certipost/OU=E-Trust/OU=NA/OU=NA/CN=Marc Jadoul (Signing))
Found 1 key:
1 P Private Key
ID = 45
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=GB, L=Test Locality, O=Organization Name, OU=Organizational Unit Name, CN=Common Name/emailAddress=te
***@email.address
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:ba:b3:b1:fb:c0:77:23:0e:62:28:6c:b9:ad:f6:
23:08:ac:7e:f6:83:3c:65:b1:a7:86:f1:74:92:51:
ba:ff:29:91:c4:3d:45:e8:a1:45:c6:a3:ec:d0:86:
79:6f:26:8a:6d:58:41:d5:56:6b:fa:5d:cf:ab:bf:
bb:8c:5b:6d:42:39:4a:40:3f:61:d2:7b:4f:63:2e:
56:b7:be:29:b0:a7:df:e7:3c:4c:3e:ee:3a:de:bb:
bd:0c:60:d8:41:fd:37:b3:f7:1e:0d:85:2f:57:bc:
22:bd:38:db:f2:1c:e9:97:b5:9f:7c:ac:f7:20:f1:
aa:8b:06:79:f9:5f:b0:72:1b
Exponent: 2593935281 (0x9a9c4fb1)
Attributes:
challengePassword :A challenge password
Signature Algorithm: md5WithRSAEncryption
ba:14:5b:d0:8e:90:af:68:cc:e3:36:98:16:ae:d9:75:df:95:
7a:f8:e4:c1:d2:f8:96:ec:15:64:2c:55:0b:c3:c2:0c:40:d5:
d6:f3:21:f7:dc:72:6e:41:9e:ae:f8:5d:17:c9:6b:92:af:bd:
ba:7e:bb:f5:42:9b:35:7a:49:f4:2b:87:92:fb:55:c8:ec:35:
2a:5f:97:91:82:c7:43:d5:0e:09:da:dc:ce:b8:d6:1c:07:e1:
54:90:71:4a:ff:e8:bb:e9:65:c5:fd:ff:62:b6:05:fb:91:64:
4a:e5:2c:28:c7:d0:49:b6:91:15:ac:0e:d3:0a:b0:27:b4:1a:
be:1a
-----BEGIN CERTIFICATE REQUEST-----
MIICBTCCAW4CAQAwgZ0xCzAJBgNVBAYTAkdCMRYwFAYDVQQHEw1UZXN0IExvY2Fs
aXR5MRowGAYDVQQKExFPcmdhbml6YXRpb24gTmFtZTEhMB8GA1UECxMYT3JnYW5p
emF0aW9uYWwgVW5pdCBOYW1lMRQwEgYDVQQDEwtDb21tb24gTmFtZTEhMB8GCSqG
SIb3DQEJARYSdGVzdEBlbWFpbC5hZGRyZXNzMIGhMA0GCSqGSIb3DQEBAQUAA4GP
ADCBiwKBgQC6s7H7wHcjDmIobLmt9iMIrH72gzxlsaeG8XSSUbr/KZHEPUXooUXG
o+zQhnlvJoptWEHVVmv6Xc+rv7uMW21COUpAP2HSe09jLla3vimwp9/nPEw+7jre
u70MYNhB/Tez9x4NhS9XvCK9ONvyHOmXtZ98rPcg8aqLBnn5X7ByGwIFAJqcT7Gg
JTAjBgkqhkiG9w0BCQcxFhMUQSBjaGFsbGVuZ2UgcGFzc3dvcmQwDQYJKoZIhvcN
AQEEBQADgYEAuhRb0I6Qr2jM4zaYFq7Zdd+VevjkwdL4luwVZCxVC8PCDEDV1vMh
99xybkGervhdF8lrkq+9un679UKbNXpJ9CuHkvtVyOw1Kl+XkYLHQ9UOCdrczrjW
HAfhVJBxSv/ou+llxf3/YrYF+5FkSuUsKMfQSbaRFawO0wqwJ7Qavho=
-----END CERTIFICATE REQUEST-----
First: I am a brand new user of opensc, and English is not my native language .
I have been trying to use etoken PRO with openssl on Linux and Windows.
The Linux implementation using the openssl+engine_opensc.so seems to work for me, knowing that I initialize the token using opensc.
But we are shipping these token to clients that use it in windows. These token have been initialized using Official PKCS11 from Alladin (eTpkcs11.dll), wich does not seems to play well with opensc.
I did try to use the etpkcs11.dll of Alladin with the statically linked version of opensc on windows (win32bin_stat_18_10_2004.zip), but get several errors, both with pkcs11-tool or with engine_pkcs11.dll.
The same eToken seems to work correctly in Firefox after registering eTpkcs11.dll and using a the token initialized with opensc and opensc-pkcs11.dll it work too.
Is this a known problem (I guess yes ;-/) and is someone able to provide a fast solution? (free or not ;-)
C:toolsopensc>pkcs11-tool.exe --module etpkcs11.dll --pin 123456 -O -v
Certificate Object, type = X.509 cert
label: Unlabeled
ID: 39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30
Public Key Object; RSA 1024 bits
label: eTCAPI public key
ID: 39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30
Usage: encrypterror: PKCS11 function C_GetAttributeValue(DECRYPT) failed: rv = CKR_ATTRIBUTE_TYPE_INVALID (0x12)
Aborting.
C:toolsopensc>openssl
OpenSSL> engine dynamic -pre SO_PATH:engine_pkcs11 -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:etpkcs11.dl
l
(dynamic) Dynamic engine loading support
[Success]: SO_PATH:engine_pkcs11
[Success]: ID:pkcs11
[Success]: LIST_ADD:1
[Success]: LOAD
[Success]: MODULE_PATH:etpkcs11.dll
Loaded: (pkcs11) pkcs11 engine
OpenSSL> engine pkcs11 -pre PIN:123456 -pre VERBOSE
(pkcs11) pkcs11 engine
[Success]: PIN:123456
[Success]: VERBOSE
OpenSSL> req -engine pkcs11 -new -key id_39453945373335312d333545442d343031612d384637302d3238463636393036363042303a30 -k
eyform engine -text -config openssl.cnf
initializing engine
engine 'pkcs11' set.
Found 2 slots
[0] AKS ifdh 0 uninitialized, login (eToken)
[1] AKS ifdh 1 no tok
Found uninitialized token;
PKCS11_get_private_key returned NULL
unable to load Private Key
2676:error:26096080:engine routines:ENGINE_load_private_key:failed loading private key:.cryptoengineeng_pkey.c:117:
error in req
With an other token initialized using opensc, on windows and using the default pkcs11 (engine+dll) everything seems to work:
C:toolsopensc>pkcs11-tool.exe --pin 123456 -O -v
Private Key Object; RSA 1024 bits
label: Private Key
ID: 45
Usage: sign
Certificate Object, type = X.509 cert
label: Certificate
ID: 45
Public Key Object; RSA 1024 bits
label: Certificate
ID: 45
Usage: encrypt, verify
C:toolsopensc>openssl
OpenSSL> engine dynamic -pre SO_PATH:engine_pkcs11 -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:opensc-pkcs11.dll
(dynamic) Dynamic engine loading support
[Success]: SO_PATH:engine_pkcs11
[Success]: ID:pkcs11
[Success]: LIST_ADD:1
[Success]: LOAD
[Success]: MODULE_PATH:opensc-pkcs11.dll
Loaded: (pkcs11) pkcs11 engine
OpenSSL> engine pkcs11 -pre PIN:123456 -pre VERBOSE
(pkcs11) pkcs11 engine
[Success]: PIN:123456
[Success]: VERBOSE
OpenSSL> req -engine pkcs11 -new -key id_45 -keyform engine -text -config openssl.cnf
initializing engine
engine 'pkcs11' set.
Found 8 slots
[0] AKS ifdh 0 login (OpenSC Card (Marc Jadoul (signin)
[1] AKS ifdh 0 (OpenSC Card)
[2] AKS ifdh 0 no pin (OpenSC Card)
[3] AKS ifdh 0 no pin (OpenSC Card)
[4] AKS ifdh 1 no tok
[5] AKS ifdh 1 no tok
[6] AKS ifdh 1 no tok
[7] AKS ifdh 1 no tok
Found slot: AKS ifdh 0
Found token: OpenSC Card (Marc Jadoul (signin
Found 1 certificate:
1 Certificate (/C=BE/L=Bruxelles/O=Certipost/OU=E-Trust/OU=NA/OU=NA/CN=Marc Jadoul (Signing))
Found 1 key:
1 P Private Key
ID = 45
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=GB, L=Test Locality, O=Organization Name, OU=Organizational Unit Name, CN=Common Name/emailAddress=te
***@email.address
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:ba:b3:b1:fb:c0:77:23:0e:62:28:6c:b9:ad:f6:
23:08:ac:7e:f6:83:3c:65:b1:a7:86:f1:74:92:51:
ba:ff:29:91:c4:3d:45:e8:a1:45:c6:a3:ec:d0:86:
79:6f:26:8a:6d:58:41:d5:56:6b:fa:5d:cf:ab:bf:
bb:8c:5b:6d:42:39:4a:40:3f:61:d2:7b:4f:63:2e:
56:b7:be:29:b0:a7:df:e7:3c:4c:3e:ee:3a:de:bb:
bd:0c:60:d8:41:fd:37:b3:f7:1e:0d:85:2f:57:bc:
22:bd:38:db:f2:1c:e9:97:b5:9f:7c:ac:f7:20:f1:
aa:8b:06:79:f9:5f:b0:72:1b
Exponent: 2593935281 (0x9a9c4fb1)
Attributes:
challengePassword :A challenge password
Signature Algorithm: md5WithRSAEncryption
ba:14:5b:d0:8e:90:af:68:cc:e3:36:98:16:ae:d9:75:df:95:
7a:f8:e4:c1:d2:f8:96:ec:15:64:2c:55:0b:c3:c2:0c:40:d5:
d6:f3:21:f7:dc:72:6e:41:9e:ae:f8:5d:17:c9:6b:92:af:bd:
ba:7e:bb:f5:42:9b:35:7a:49:f4:2b:87:92:fb:55:c8:ec:35:
2a:5f:97:91:82:c7:43:d5:0e:09:da:dc:ce:b8:d6:1c:07:e1:
54:90:71:4a:ff:e8:bb:e9:65:c5:fd:ff:62:b6:05:fb:91:64:
4a:e5:2c:28:c7:d0:49:b6:91:15:ac:0e:d3:0a:b0:27:b4:1a:
be:1a
-----BEGIN CERTIFICATE REQUEST-----
MIICBTCCAW4CAQAwgZ0xCzAJBgNVBAYTAkdCMRYwFAYDVQQHEw1UZXN0IExvY2Fs
aXR5MRowGAYDVQQKExFPcmdhbml6YXRpb24gTmFtZTEhMB8GA1UECxMYT3JnYW5p
emF0aW9uYWwgVW5pdCBOYW1lMRQwEgYDVQQDEwtDb21tb24gTmFtZTEhMB8GCSqG
SIb3DQEJARYSdGVzdEBlbWFpbC5hZGRyZXNzMIGhMA0GCSqGSIb3DQEBAQUAA4GP
ADCBiwKBgQC6s7H7wHcjDmIobLmt9iMIrH72gzxlsaeG8XSSUbr/KZHEPUXooUXG
o+zQhnlvJoptWEHVVmv6Xc+rv7uMW21COUpAP2HSe09jLla3vimwp9/nPEw+7jre
u70MYNhB/Tez9x4NhS9XvCK9ONvyHOmXtZ98rPcg8aqLBnn5X7ByGwIFAJqcT7Gg
JTAjBgkqhkiG9w0BCQcxFhMUQSBjaGFsbGVuZ2UgcGFzc3dvcmQwDQYJKoZIhvcN
AQEEBQADgYEAuhRb0I6Qr2jM4zaYFq7Zdd+VevjkwdL4luwVZCxVC8PCDEDV1vMh
99xybkGervhdF8lrkq+9un679UKbNXpJ9CuHkvtVyOw1Kl+XkYLHQ9UOCdrczrjW
HAfhVJBxSv/ou+llxf3/YrYF+5FkSuUsKMfQSbaRFawO0wqwJ7Qavho=
-----END CERTIFICATE REQUEST-----